Automate What Takes Hours
Security teams spend 80% of their time on manual threat hunting. We automate it all.

Security teams waste hours compiling reports from dozens of tools
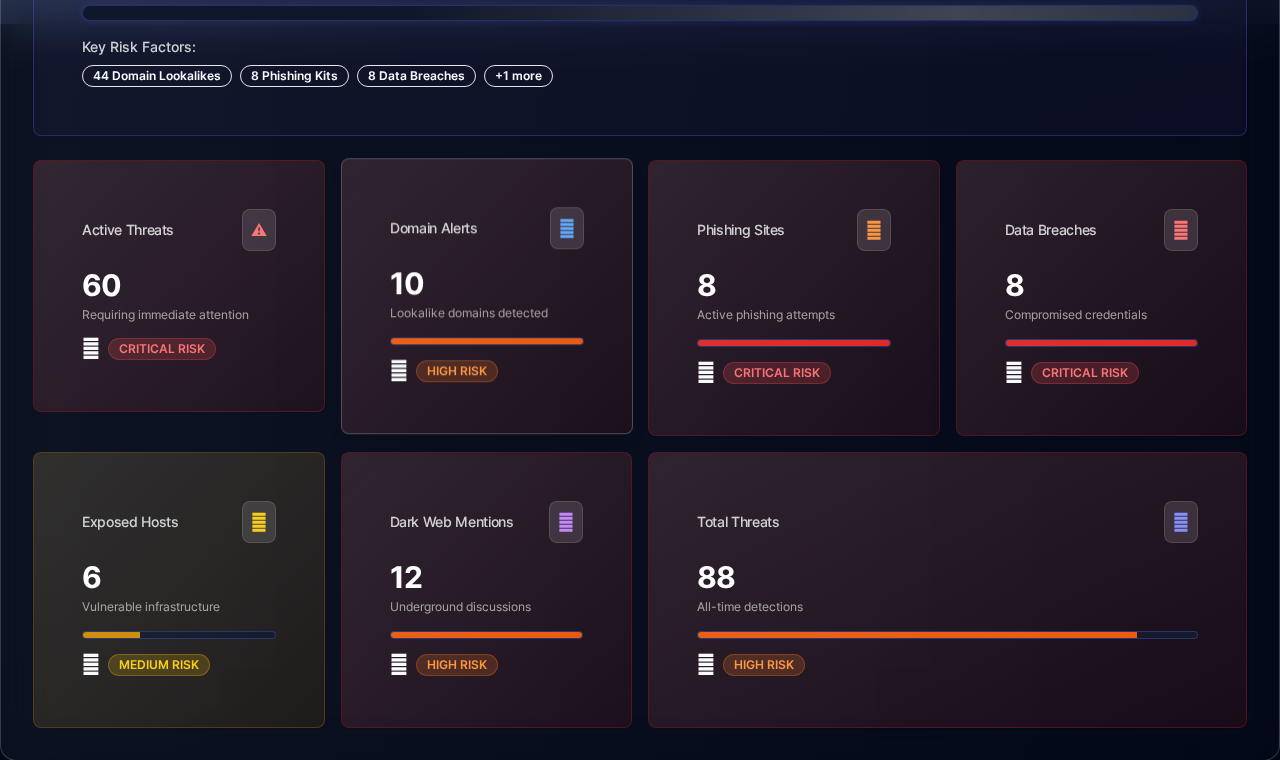
Know Your Security Posture in 60 Seconds
Get instant visibility across 15 threat intelligence layers in a single dashboard
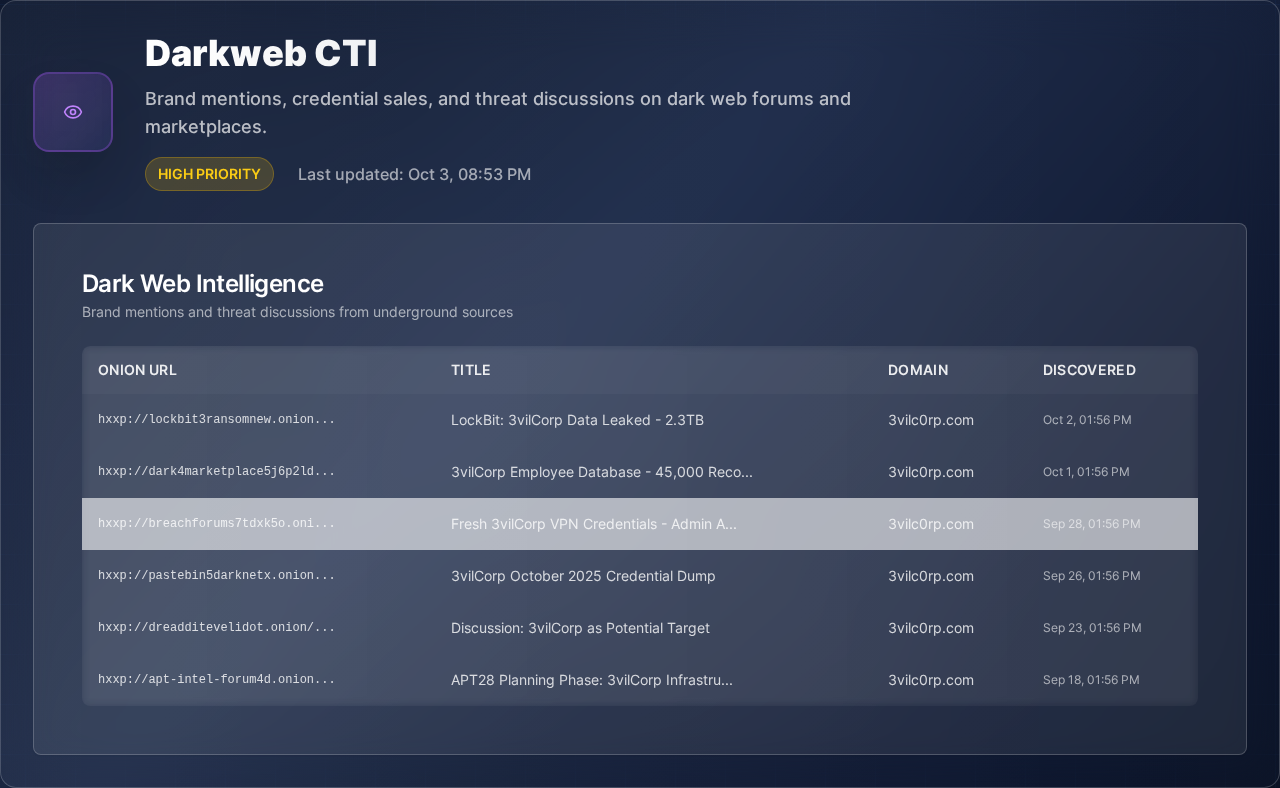
By the time you discover a breach, attackers have had your credentials for weeks
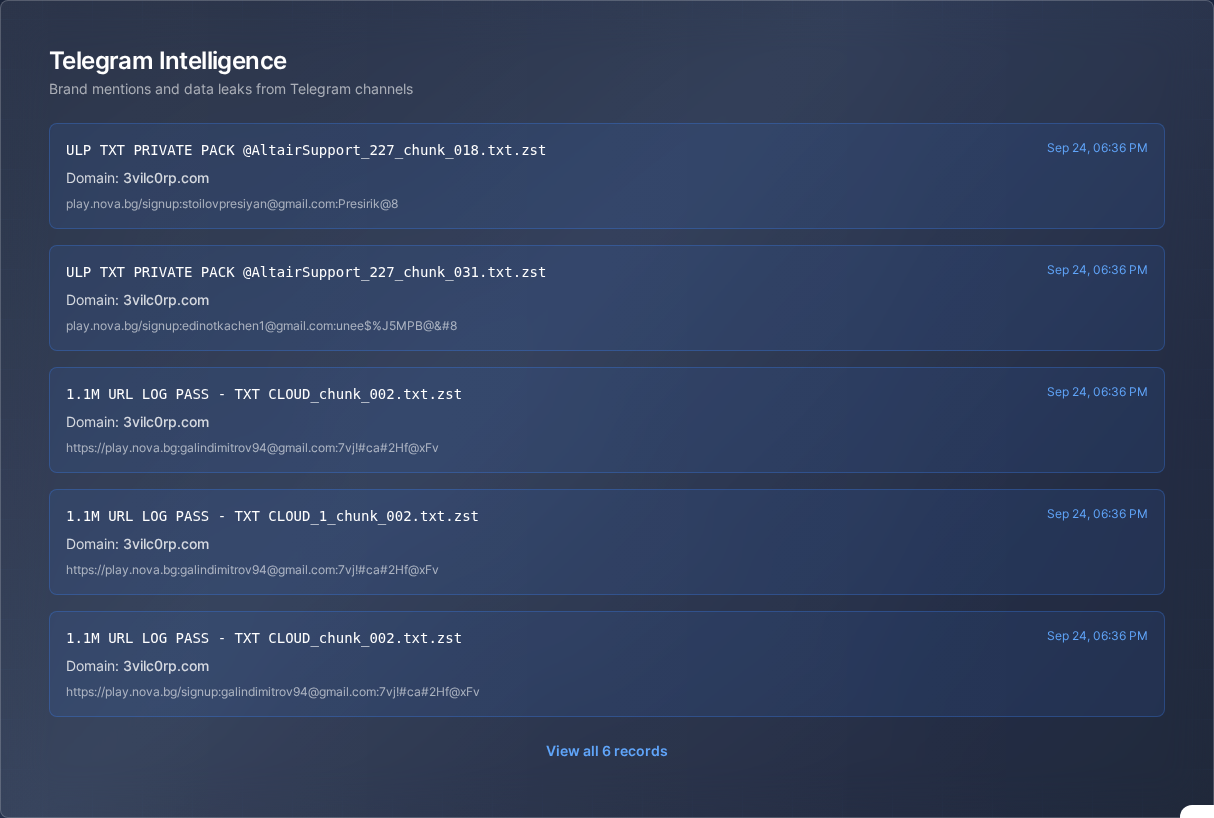
Catch Credential Theft Before the Attack
Monitor dark web marketplaces and Telegram channels where stolen data appears first

Threat intelligence requires manually monitoring hundreds of Telegram channels
Stop Living Inside Telegram Groups
AI scans 10,000+ dark channels automatically, alerts you to relevant threats only
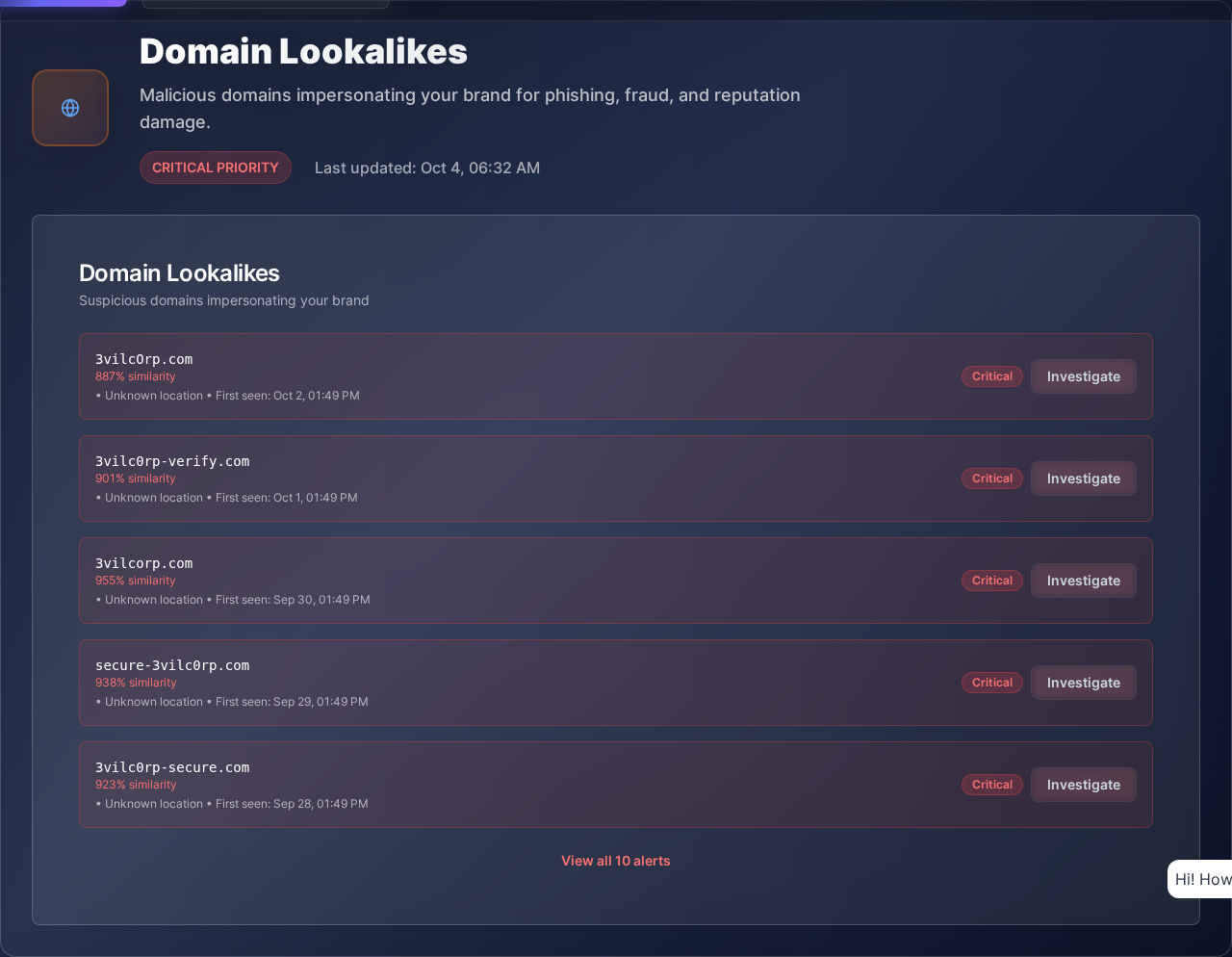
Phishing sites clone your brand and steal customer credentials for weeks before takedown
Shut Down Phishing Sites Automatically
Detect lookalike domains in minutes, initiate automated takedown within hours
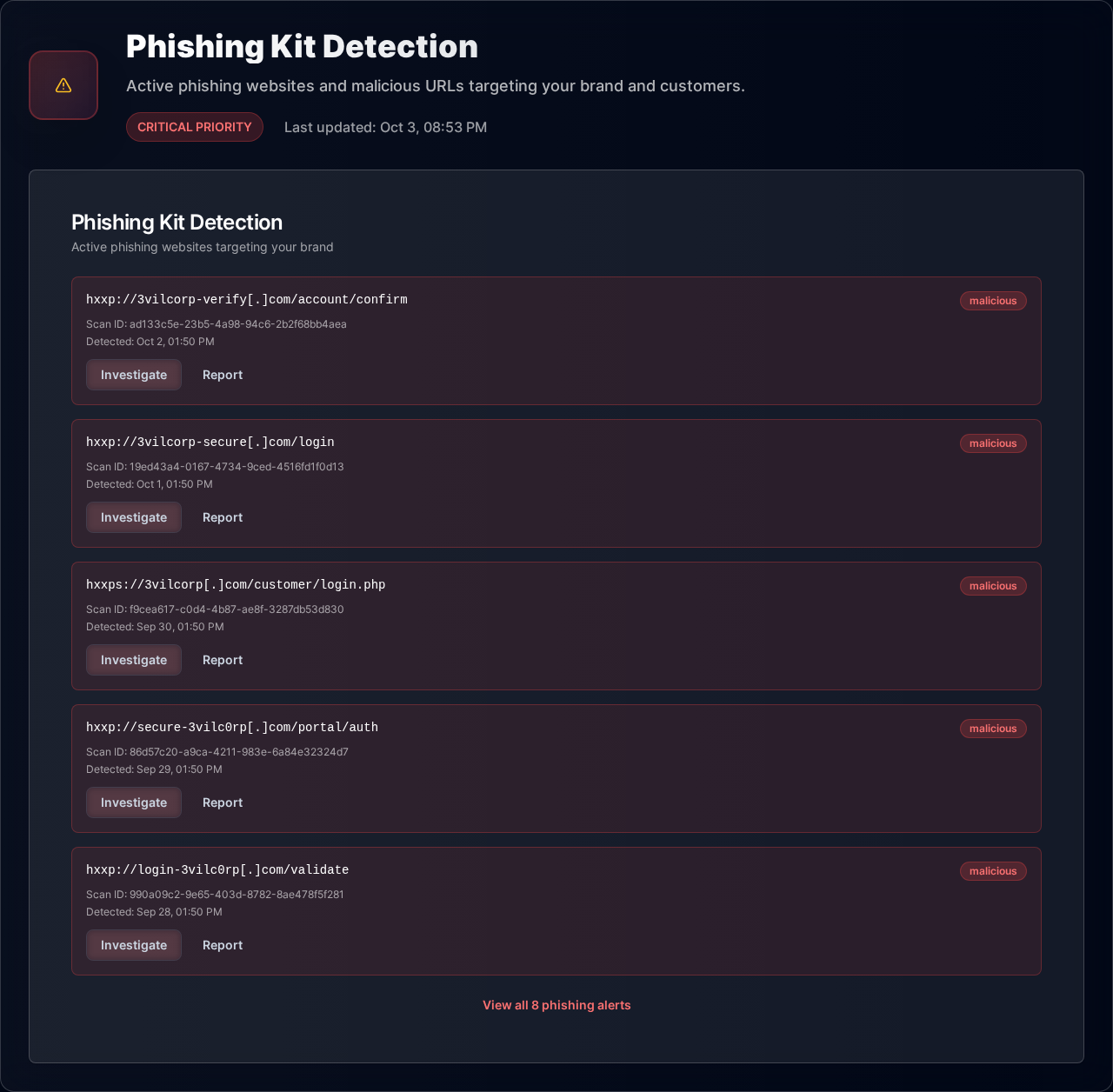
Attackers test phishing infrastructure weeks before launching campaigns
Find Phishing Kits Before They Go Live
Detect phishing kits during development, shut them down before any damage
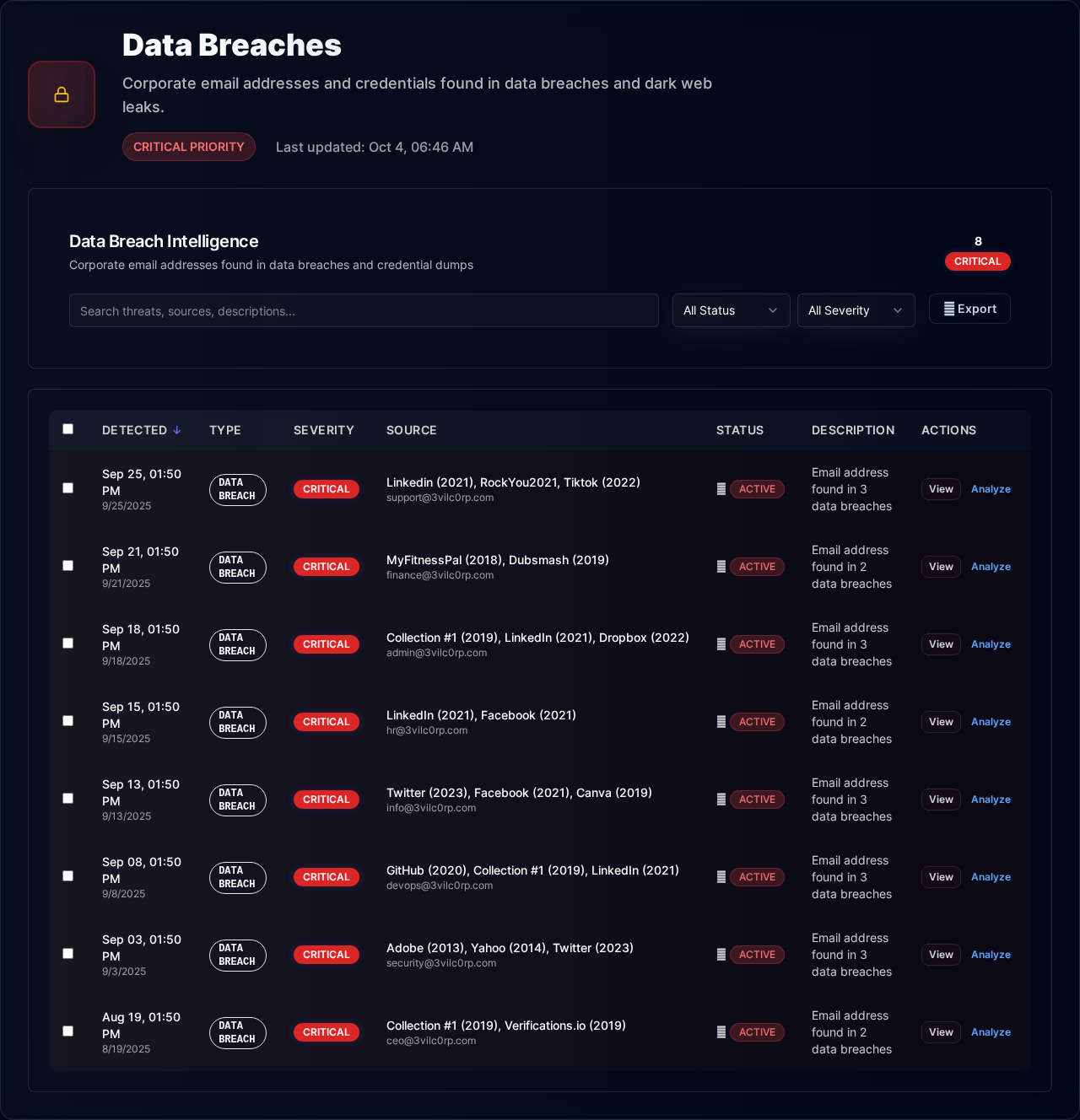
Employee credentials in data breaches expose your organization for months
Know When Your Employees Are Compromised
Monitor every major breach and dark web leak, get instant alerts when your emails appear
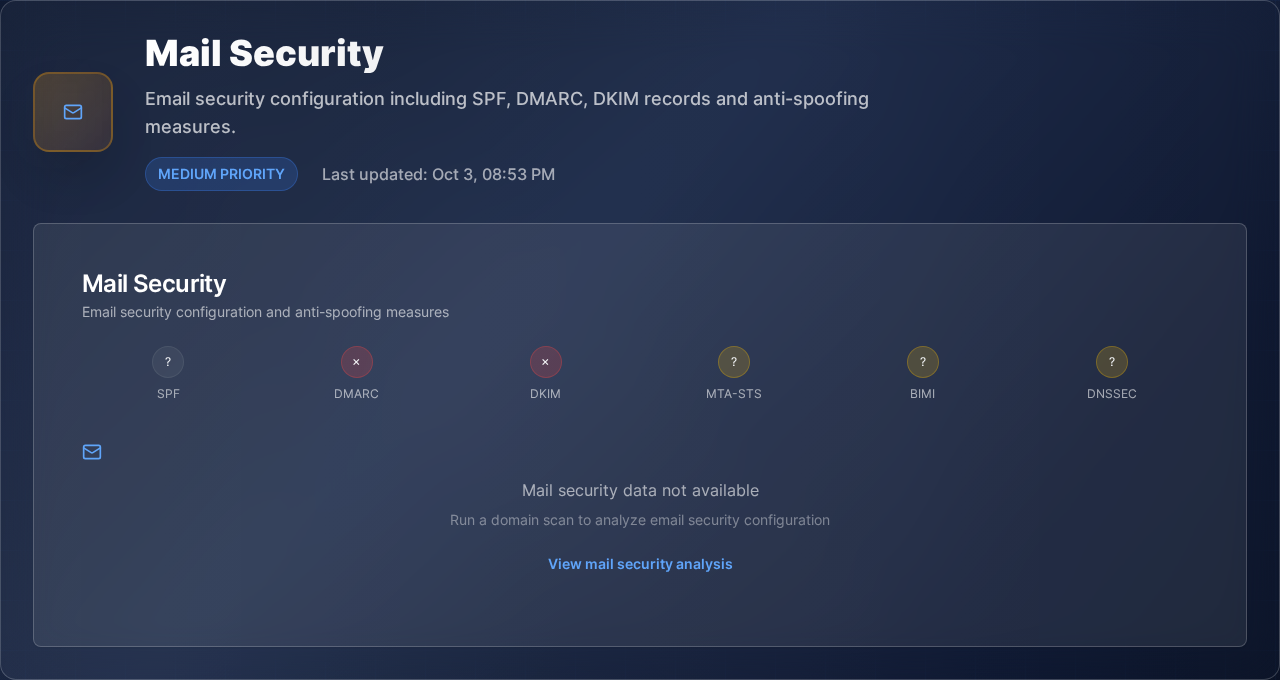
Email security misconfigurations allow attackers to impersonate your domain
Stop Email Spoofing in 5 Minutes
Automated SPF/DMARC/DKIM analysis with guided fixes - no security expertise needed
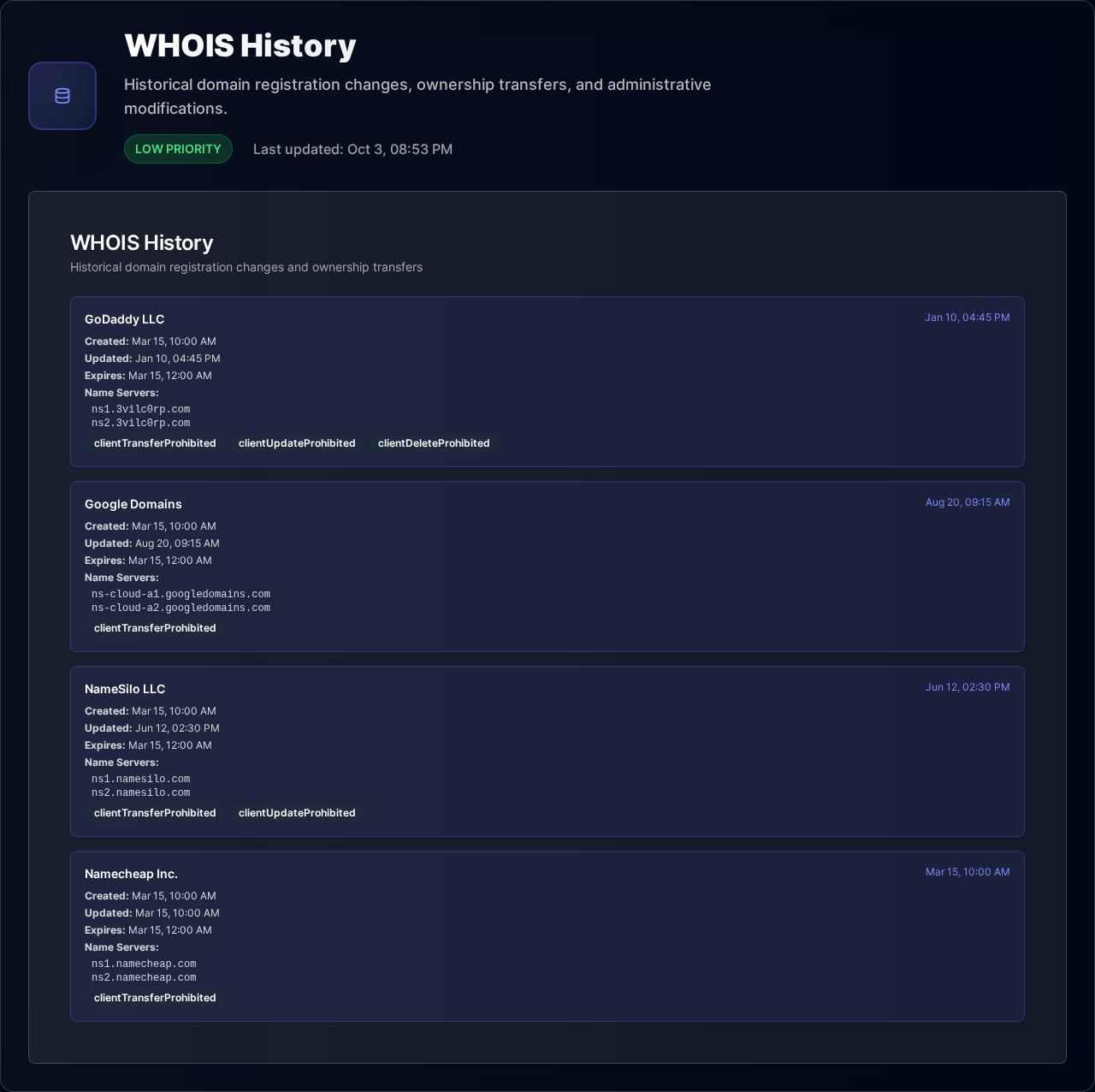
Domain ownership changes go unnoticed until it's too late
Catch Domain Hijacking Attempts Early
Track every WHOIS change, get instant alerts on suspicious modifications
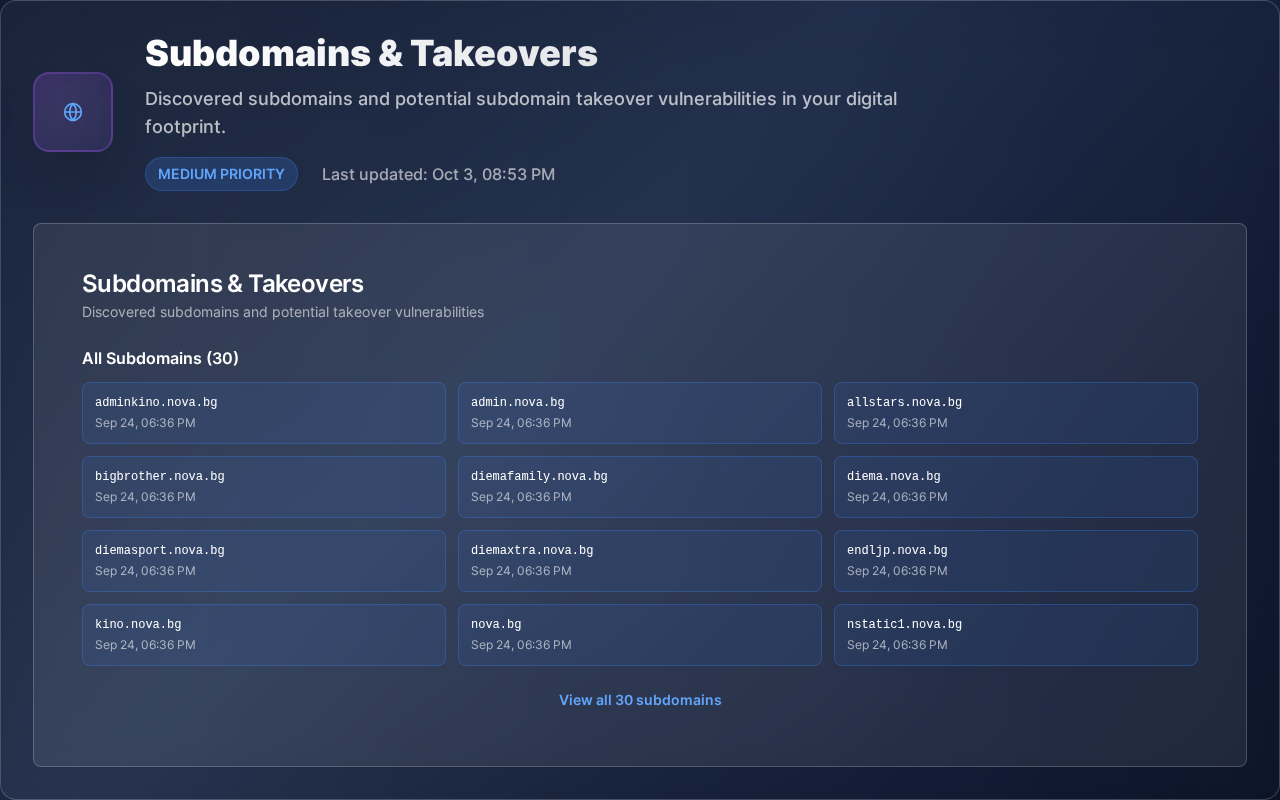
Abandoned subdomains become entry points for attackers
Find Vulnerable Subdomains Before Hackers Do
Continuous subdomain discovery and takeover vulnerability scanning
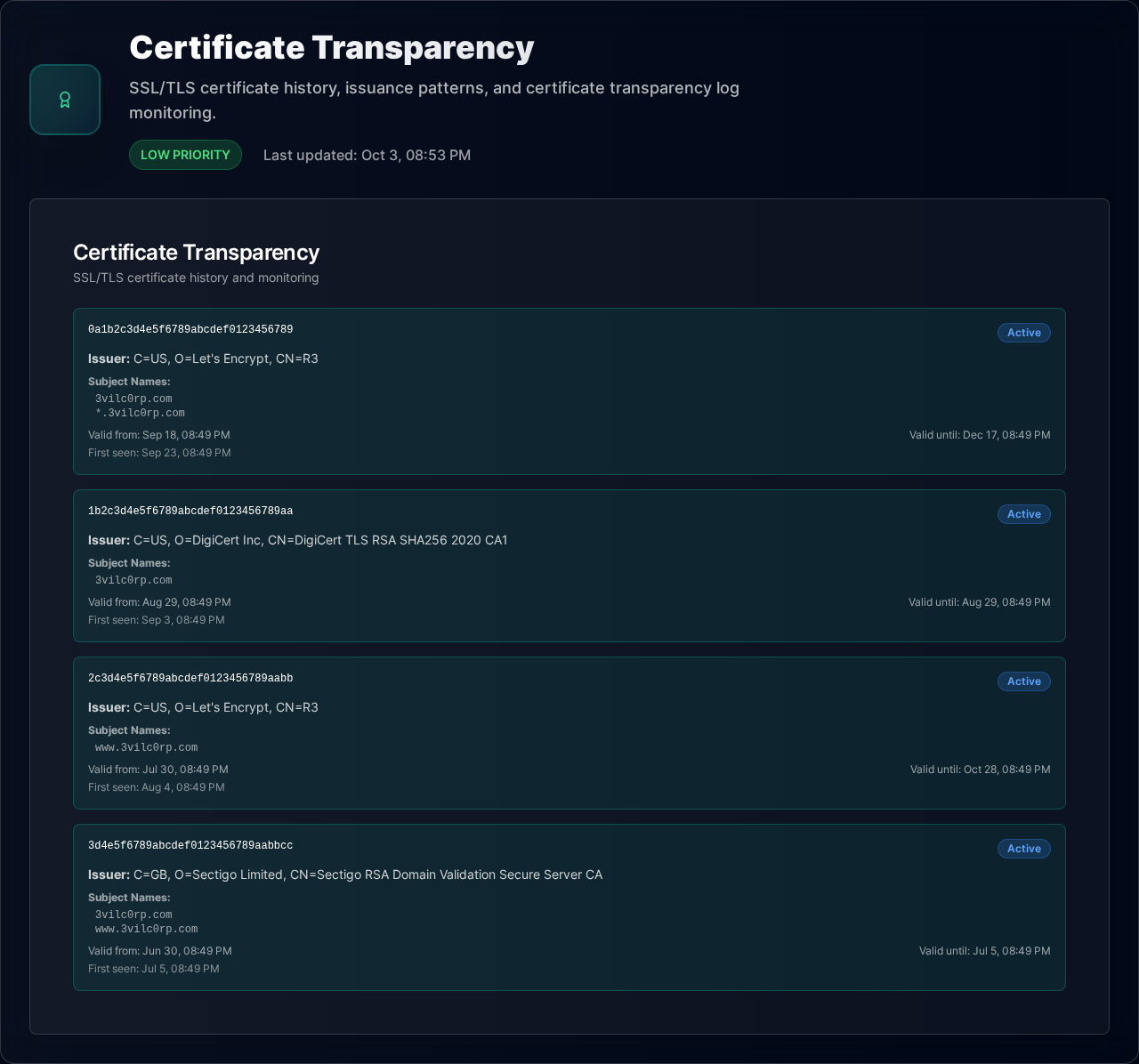
Rogue SSL certificates enable undetected interception of customer data
Prevent Man-in-the-Middle Attacks
Monitor certificate transparency logs, detect unauthorized certs within minutes
Manually mapping threats to MITRE framework takes hours of analyst time
Map Threats to MITRE ATT&CK Automatically
AI automatically maps detected threats to tactics, techniques, and procedures
See Your Threats in 48 Hours - Free
Get a complete threat intelligence report for your domain. No credit card. No commitment. Just real threats you didn't know existed.